
목차
공식 홈페이지
istioctl 설치
Mac 을 사용하는 경우 HomeBrew 를 이용해 istioctl 을 설치할 수 있습니다.
다른 OS 를 사용하거나 특정 버전의 Istio 를 사용하고 싶은 경우 다음과 같이 Istio 버전을 Setting 한 후 해당 버전을 내려받아 사용할 수 있습니다.
export ISTIO_VERSION=1.14.5
curl -L https://istio.io/downloadIstio | ISTIO_VERSION=$ISTIO_VERSION TARGET_ARCH=x86_64 sh -
|
Istio Profile 설치
istioctl install --set profile=demo --set hub=gcr.io/istio-release
|
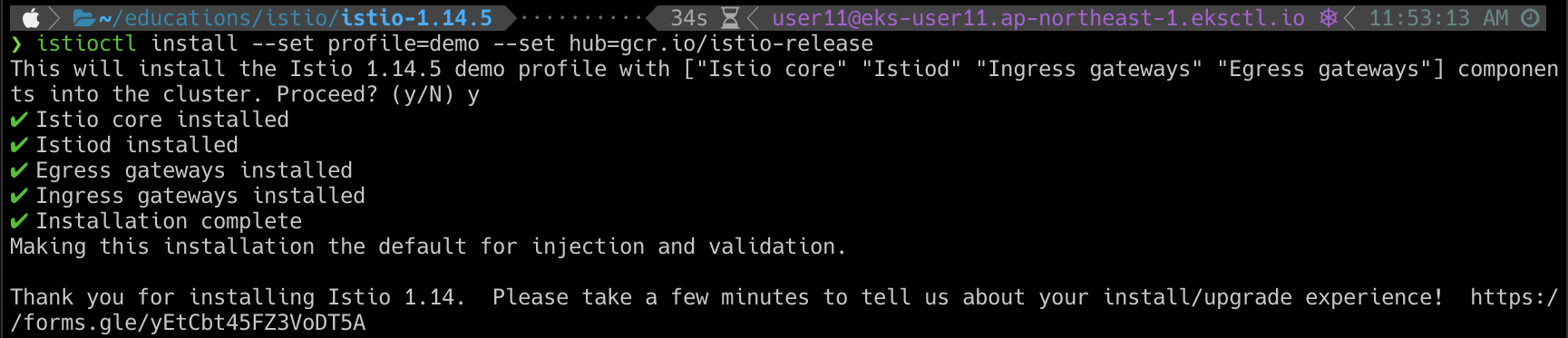
kubectl apply -f samples/addons
|
설치된 Istio Resource
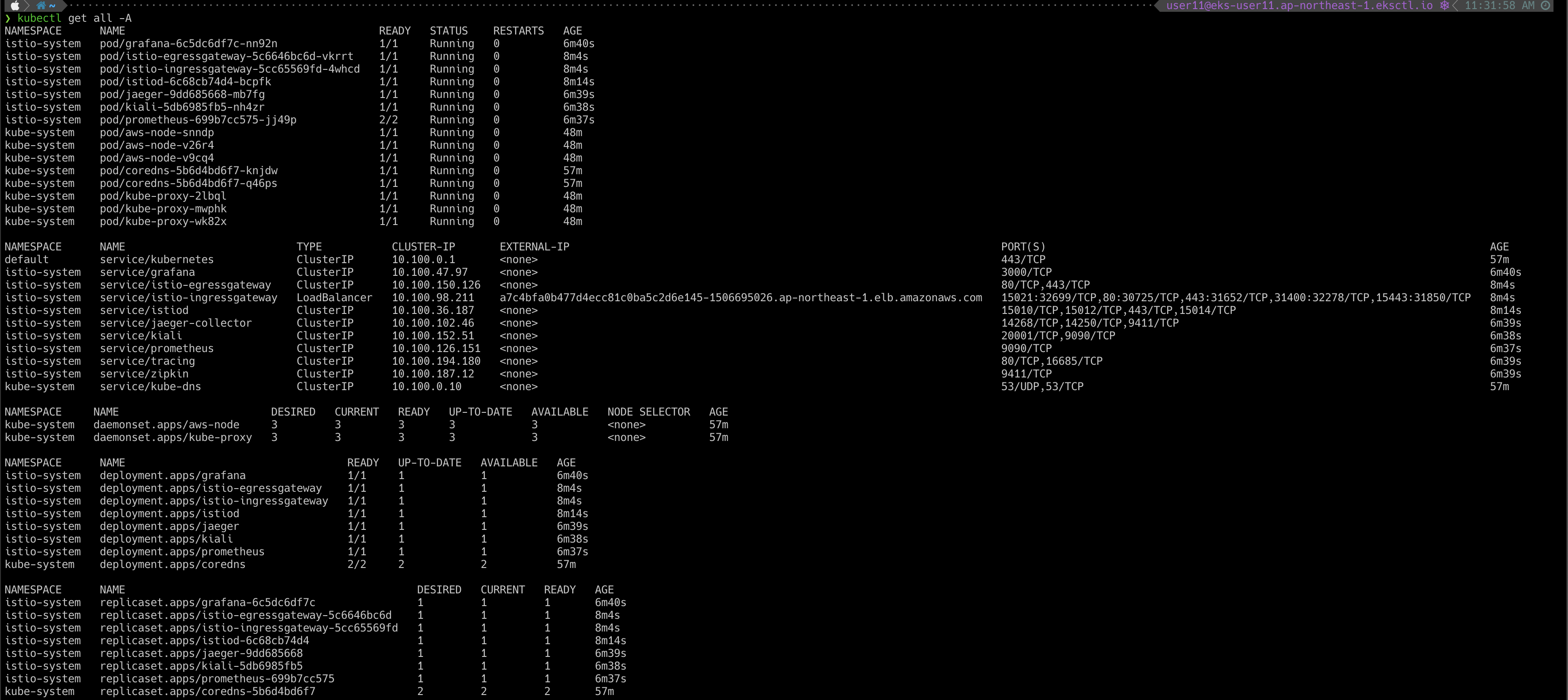
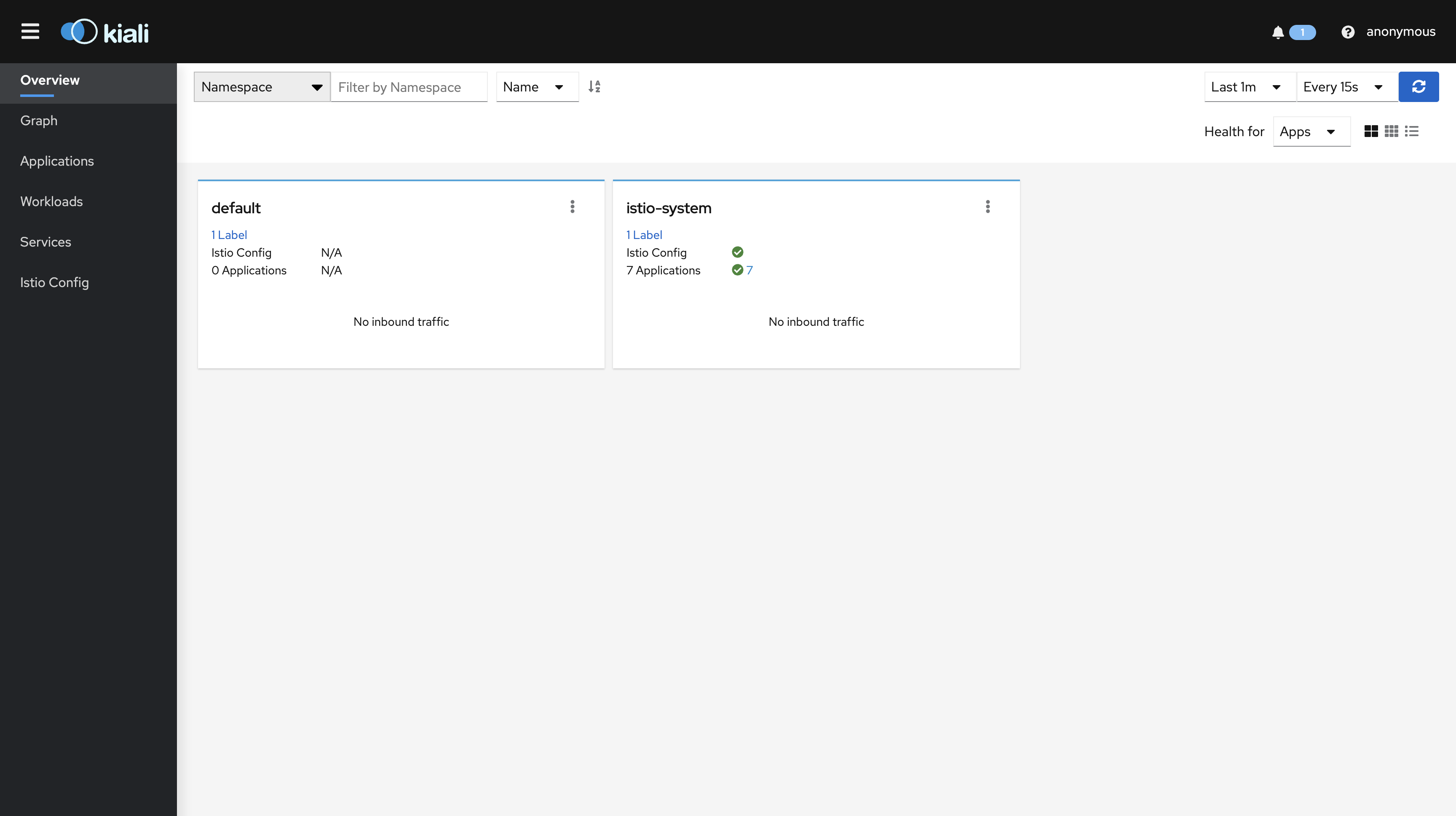
Kiali
외부에서 접근이 가능하도록 Kiali Service 를 ClusterIP 에서 LoadBalancer 로 변경합니다
kubectl patch svc kiali -n istio-system -p '{"spec": {"type": "LoadBalancer"}}'
|
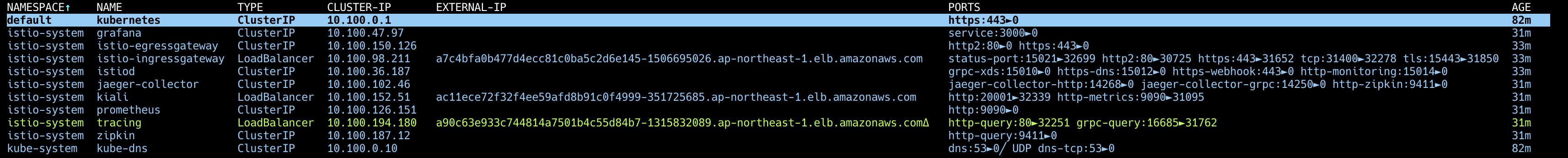
LoadBalancer 로 변경 되면서 EXTERNAL-IP 가 추가된 것을 확인할 수 있습니다.
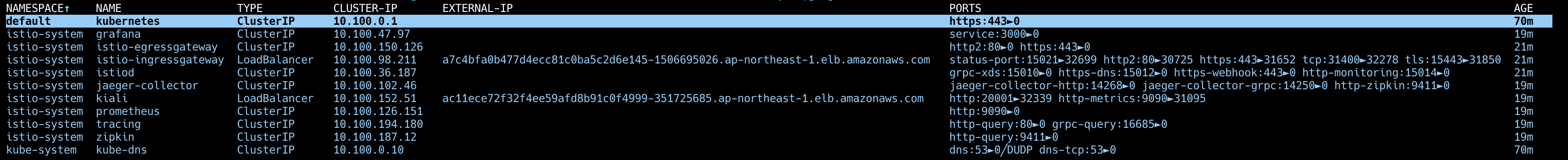
EXTERNAL-IP 를 이용해 접근하면 Kiali Dashboard 로 접근할 수 있습니다.
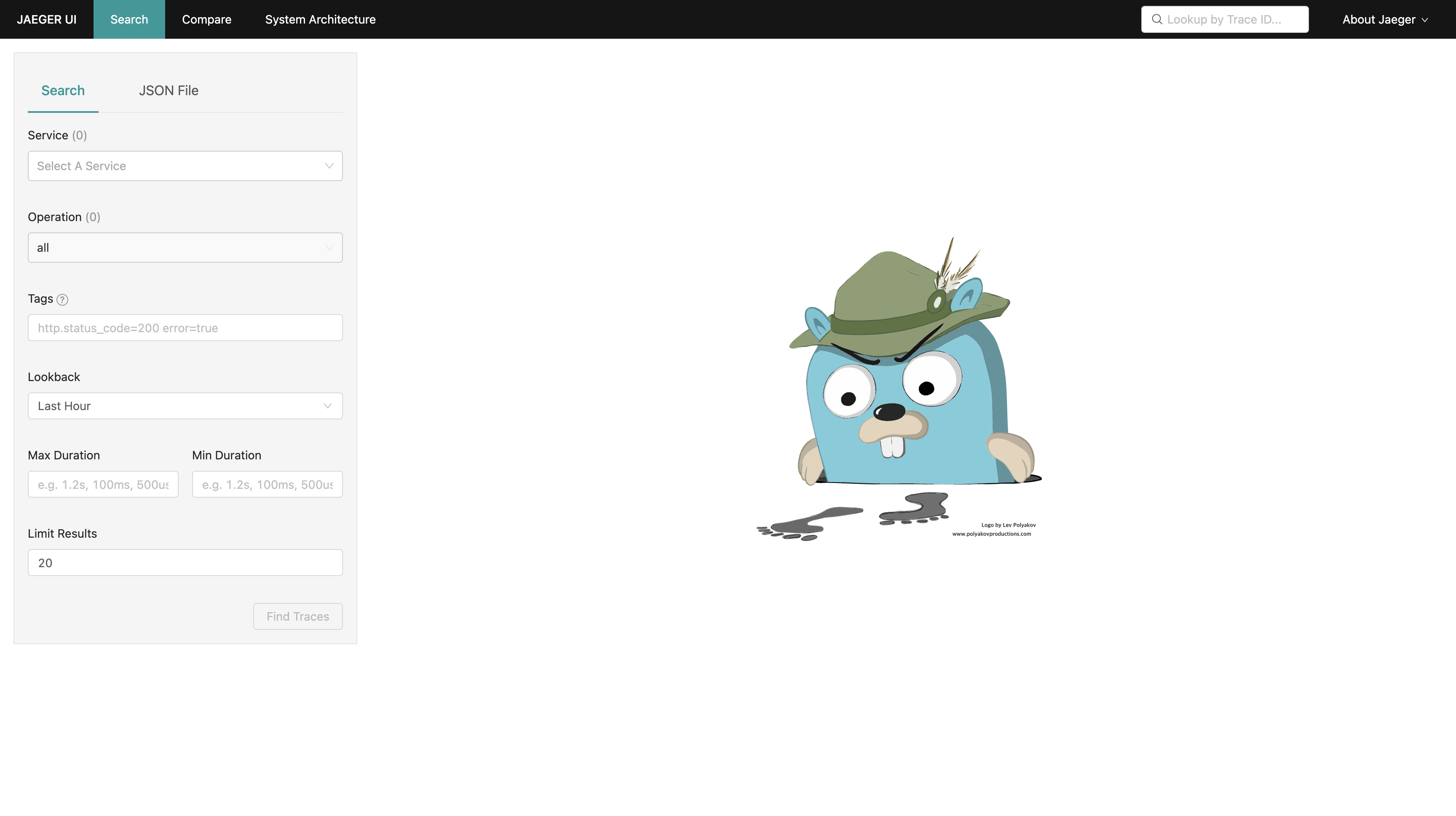
Jaeger
외부에서 접근이 가능하도록 Jaeger Service 를 ClusterIP 에서 LoadBalancer 로 변경합니다.
kubectl patch svc tracing -n istio-system -p '{"spec": {"type": "LoadBalancer"}}'
|
LoadBalancer 로 변경 되면서 EXTERNAL-IP 가 추가된 것을 확인할 수 있다.
EXTERNAL-IP 를 이용해 접근하면 Jaeger Dashboard 로 접근할 수 있습니다.
Sidecar Injection 방법
Istioctl kube-inject Command 를 이용하는 방법
kubectl apply -f <(istioctl kube-inject -f Deployment.yml)
|
- Namespace 에
istio-injection 을 enabled 로 설정하는 방법
kubectl label namespace tutorial istio-injection=enabled
|
Tutorial
kubectl create namespace tutorial
|
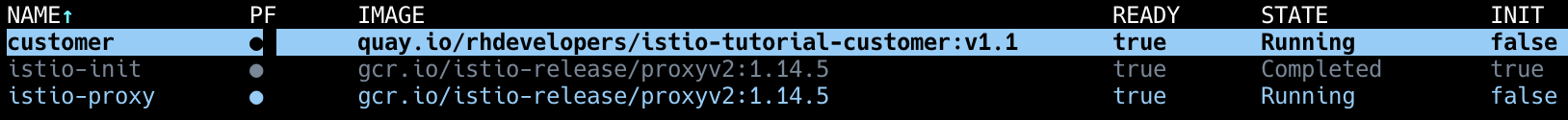
Deployment 를 설치 할때 istioctl kube-inject 명령어를 통해 Istio Container 가 Pod 내에 설치되도록 설정합니다.
kubectl apply -f <(istioctl kube-inject -f customer/kubernetes/Deployment.yml) -n tutorial
kubectl create -f customer/kubernetes/Service.yml -n tutorial
|
Pod 가 생성될때 내부에 Istio Container 가 생성된 것을 확인할 수 있습니다.
Istio Gateway 설치 및 Customer 서비스 라우팅(VirtualService) 설정
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: customer-gateway
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- "*"
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: customer-gateway
spec:
hosts:
- "*"
gateways:
- customer-gateway
http:
- match:
- uri:
prefix: /customer
rewrite:
uri: /
route:
- destination:
host: customer
port:
number: 8080
|
kubectl apply -f customer/kubernetes/Gateway.yml -n tutorial
|
kubectl apply -f <(istioctl kube-inject -f preference/kubernetes/Deployment.yml) -n tutorial
kubectl create -f preference/kubernetes/Service.yml -n tutorial
kubectl apply -f <(istioctl kube-inject -f recommendation/kubernetes/Deployment.yml) -n tutorial
kubectl create -f recommendation/kubernetes/Service.yml -n tutorial
|
Istio - Traffic Routing
kubectl apply -f <(istioctl kube-inject -f recommendation/kubernetes/Deployment-v2.yml) -n tutorial
|
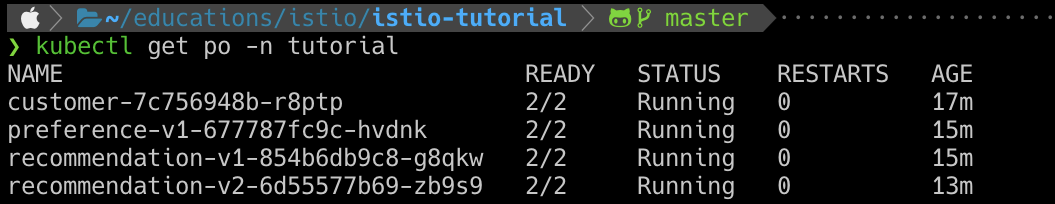
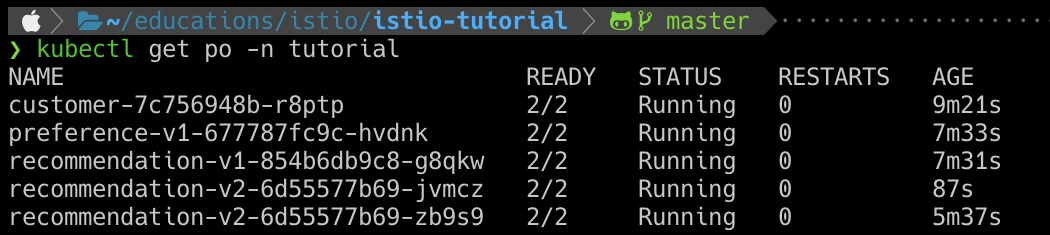
kubectl scale --replicas=2 deployment/recommendation-v2 -n tutorial
kubectl get po -n tutorial
|
kubectl get VirtualService -n tutorial -o yaml
kubectl get DestinationRule -n tutorial -o yaml
|
Istio Timeout & Retry
Timeout 설정
kubectl apply -f - <<EOF
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: vs-order-network-rule
namespace: tutorial
spec:
hosts:
- order
http:
- route:
- destination:
host: order
timeout: 3s
EOF
|
Siege 생성
kubectl apply -f - <<EOF
apiVersion: v1
kind: Pod
metadata:
name: siege
namespace: tutorial
spec:
containers:
- name: siege
image: apexacme/siege-nginx
EOF
|
kubectl exec -it siege -c siege -n tutorial -- /bin/bash
siege -c1 -t2S -v --content-type "application/json" 'http://order:8080/orders POST {"productId": "1001", "qty":5}'
|
siege -c30 -t20S -v --content-type "application/json" 'http://order:8080/orders POST {"productId": "1001", "qty":5}'
|
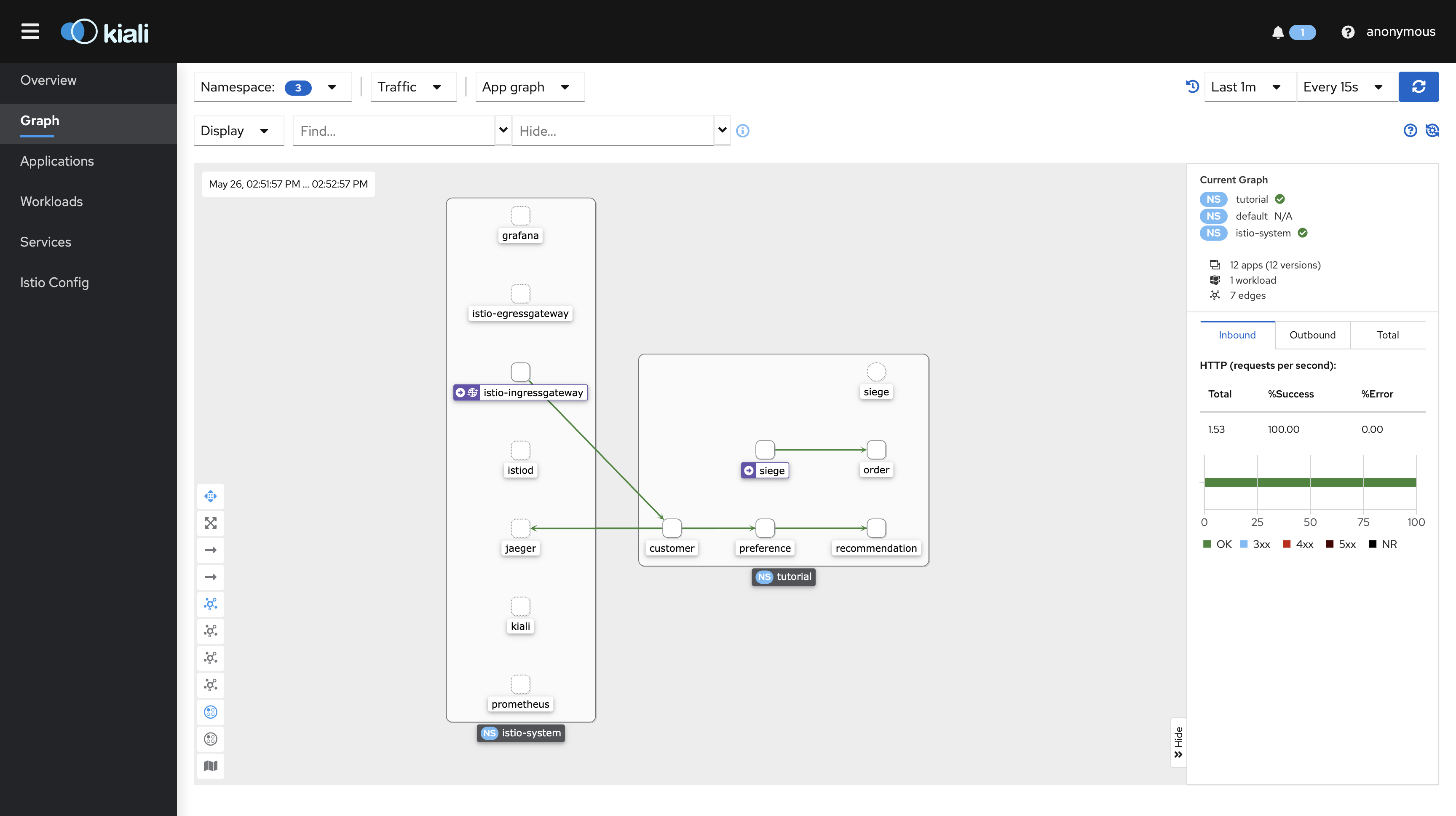
Order 서비스에 ‘Retry’ Rule 추가
kubectl apply -f - <<EOF
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: vs-order-network-rule
namespace: tutorial
spec:
hosts:
- order
http:
- route:
- destination:
host: order
timeout: 3s
retries:
attempts: 3
perTryTimeout: 2s
retryOn: 5xx,retriable-4xx,gateway-error,connect-failure,refused-stream
EOF
|
apiVersion: networking.k8s.io/v1
kind: "Ingress"
metadata:
name: "shopping-ingress"
namespace: "istio-system"
annotations:
nginx.ingress.kubernetes.io/ssl-redirect: "false"
ingressclass.kubernetes.io/is-default-class: "true"
spec:
ingressClassName: nginx
rules:
- host: "kiali.service.com"
http:
paths:
-
path: /
pathType: Prefix
backend:
service:
name: kiali
port:
number: 20001
- host: "prom.service.com"
http:
paths:
-
path: /
pathType: Prefix
backend:
service:
name: prometheus
port:
number: 9090
- host: "gra.service.com"
http:
paths:
-
path: /
pathType: Prefix
backend:
service:
name: grafana
port:
number: 3000
- host: "tracing.service.com"
http:
paths:
-
path: /
pathType: Prefix
backend:
service:
name: tracing
port:
number: 80
|
Prometheus/Grafana기반 K8s 통합 모니터링
kubectl create ns shop
kubectl label namespace shop istio-injection=enabled
kubectl apply -f https://raw.githubusercontent.com/acmexii/demo/master/edu/order-liveness.yaml -n shop
kubectl expose deploy order --port=8080 -n shop
kubectl apply -f https://raw.githubusercontent.com/acmexii/demo/master/edu/delivery-rediness-v1.yaml -n shop
kubectl expose deploy delivery --port=8080 -n shop
kubectl apply -f https://raw.githubusercontent.com/acmexii/demo/master/edu/siege-pod.yaml -n shop
|
kubectl patch service/prometheus -n istio-system -p '{"spec": {"type": "LoadBalancer"}}'
|
kubectl patch service/grafana -n istio-system -p '{"spec": {"type": "LoadBalancer"}}'
|
Istio 삭제 방법
cd istio-$ISTIO_VERSION
kubectl delete -f samples/addons
istioctl manifest generate --set profile=demo | kubectl delete --ignore-not-found=true -f -
|
kubectl delete namespace istio-system
|













