
목차
- [쿠버네티스 DevOps 구축] - OpenSearch 설치하기
- [쿠버네티스 DevOps 구축] - Prometheus 와 Grafana 설치하기
- [쿠버네티스 DevOps 구축] - Keycloak 설치하기
- [쿠버네티스 DevOps 구축] - Ingress Nginx Controller 설치하기
- [쿠버네티스 DevOps 구축] - Local PC 쿠버네티스 동적 프로비저닝을 위한 StorageClass 설치
- [쿠버네티스 DevOps 구축] - Local PC 에 쿠버네티스 설치하기
참고
- https://blog.pages.kr/2844
- https://opendistro.github.io/for-elasticsearch-docs/docs/security/access-control/api/#reserved-and-hidden-resources
- https://forum.opensearch.org/t/default-password-reset/102/10
- Admin Password 변경
✅ OpenSearch 설치
# Helm Repo 추가 |
Release "opensearch" has been upgraded. Happy Helming! |
✅ OpenSearch Dashboard 설치
helm upgrade --install opensearch-dashboard \ |
Release "opensearch" has been upgraded. Happy Helming! |
OpenSearch Demo User
Admin 비밀번호 변경
필요한 명령어 및 파일 위치
/usr/share/elasticsearch/plugins/opendistro_security/tools/hash.sh |
securityConfig: |
문제 - Not yet initialized (you may need to run securityadmin)
[2023-12-30T15:22:45,111][ERROR][o.o.s.a.BackendRegistry ] [opensearch-cluster-master-0] Not yet initialized (you may need to run securityadmin) |
kubectl -n logging exec -it opensearch-cluster-master-0 -- /usr/share/opensearch/plugins/opensearch-security/tools/hash.sh |
- pod 내에서
/usr/share/opensearch/plugins/opensearch-security/tools/securityadmin.sh \ |
- 쿠버네티스 명령어로 실행
kubectl exec \ |
securityConfig.internalUsersSecret 을 이용한 Admin 비밀번호 변경
비밀번호 Hash 값 생성
kubectl -n logging exec -it opensearch-cluster-master-0 -- /usr/share/opensearch/plugins/opensearch-security/tools/hash.sh |
Secret 파일 생성
apiVersion: v1 |
securityConfig.internalUsersSecret 에 Secret 이름 설정
securityConfig: |
✅ OpenSearch Dashboards basePath 및 Ingress 설정
config: |
Ingress 설정
apiVersion: networking.k8s.io/v1 |
✅ KeyCloak OpenSearch 연동
- 참고
- https://velog.io/@ziggy/Keyclock-%EA%B5%AC%EC%B6%95-%EB%B0%8F-Opensearch-%EC%97%B0%EB%8F%99
- https://opensearch.org/docs/latest/security/authentication-backends/openid-connect/
- https://opensearch.org/docs/latest/security/authentication-backends/openid-connect/#opensearch-security-configuration
- https://opensearch.org/docs/latest/security/authentication-backends/openid-connect/#opensearch-dashboards-single-sign-on
- https://forum.opensearch.org/t/opensearch-integration-with-keycloak-using-k8s-opster-operator/15388/5
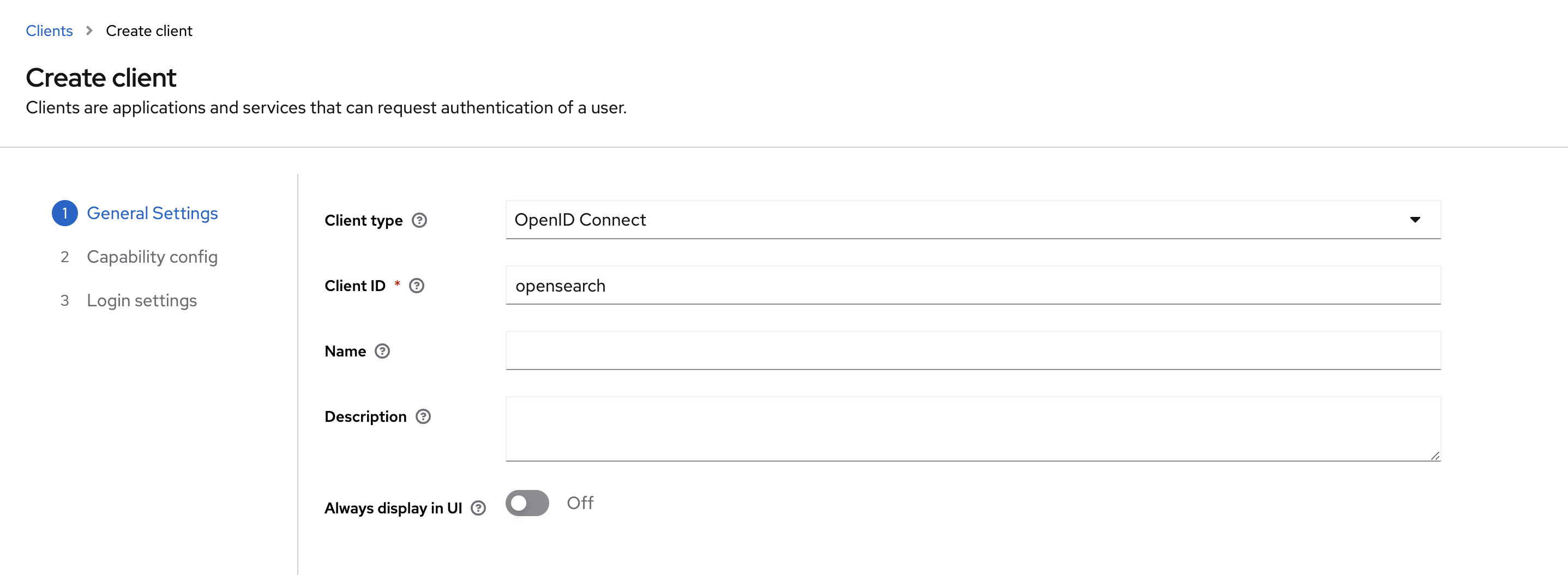
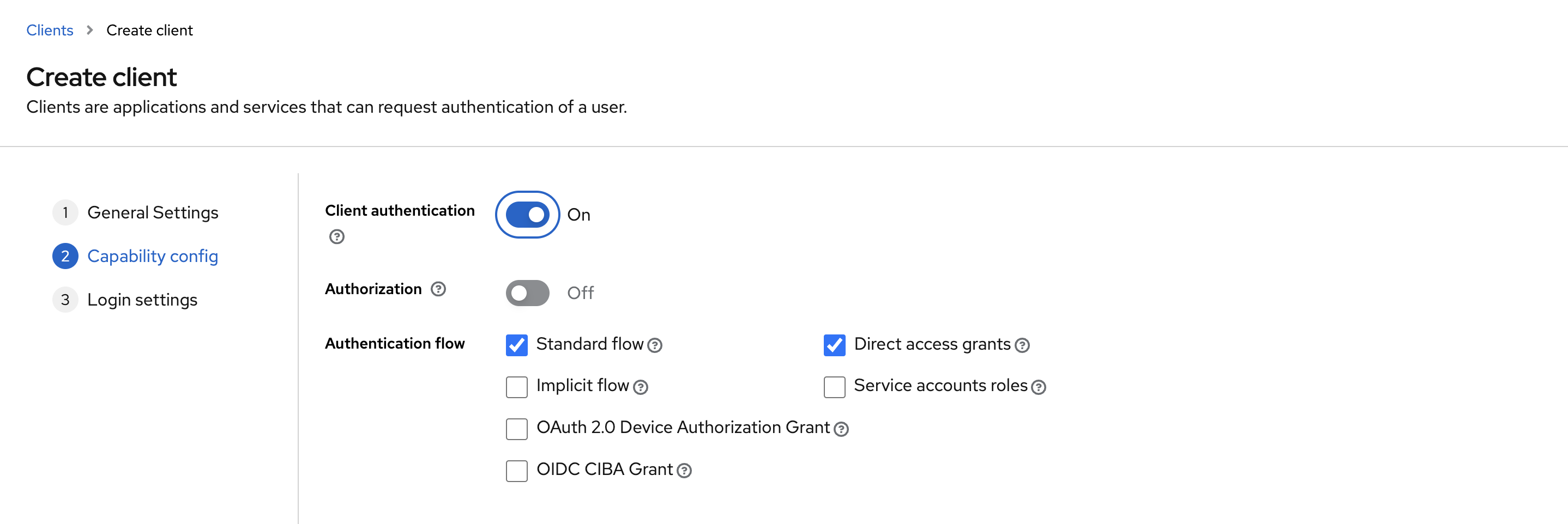
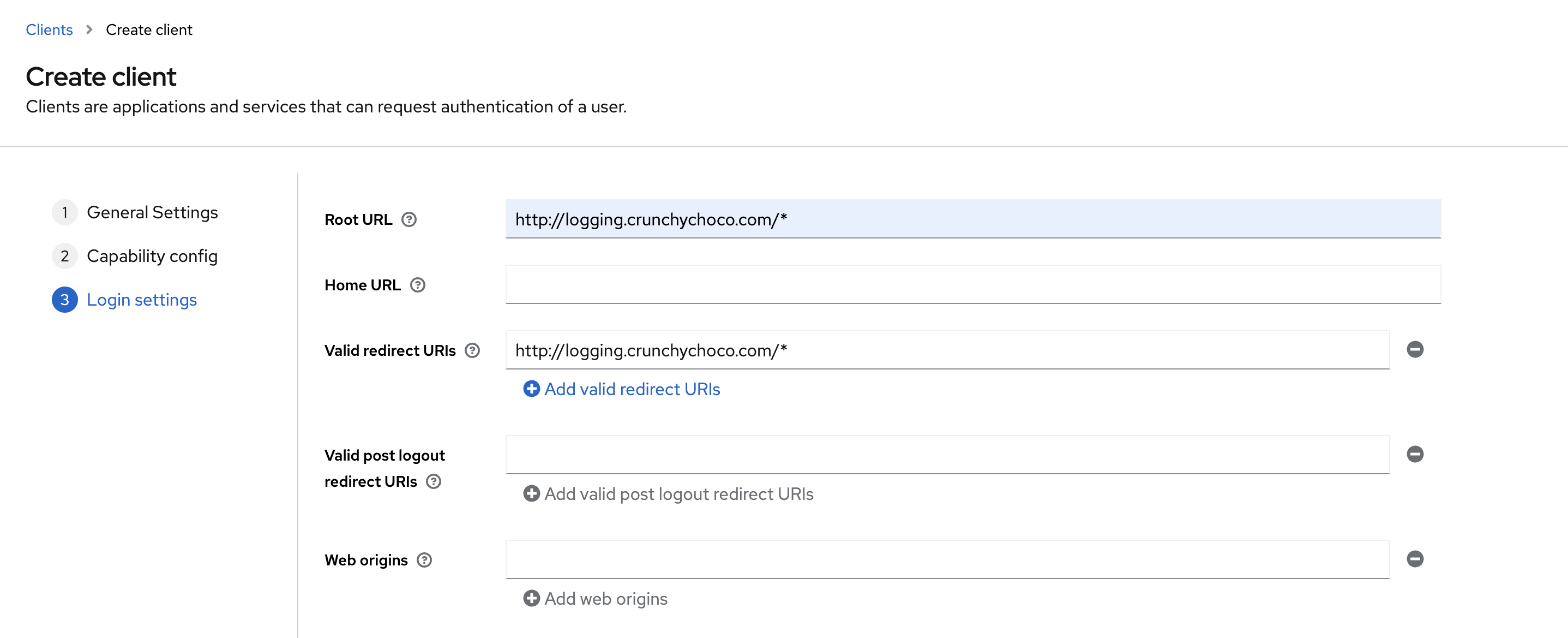
1. OpenSearch Client 생성
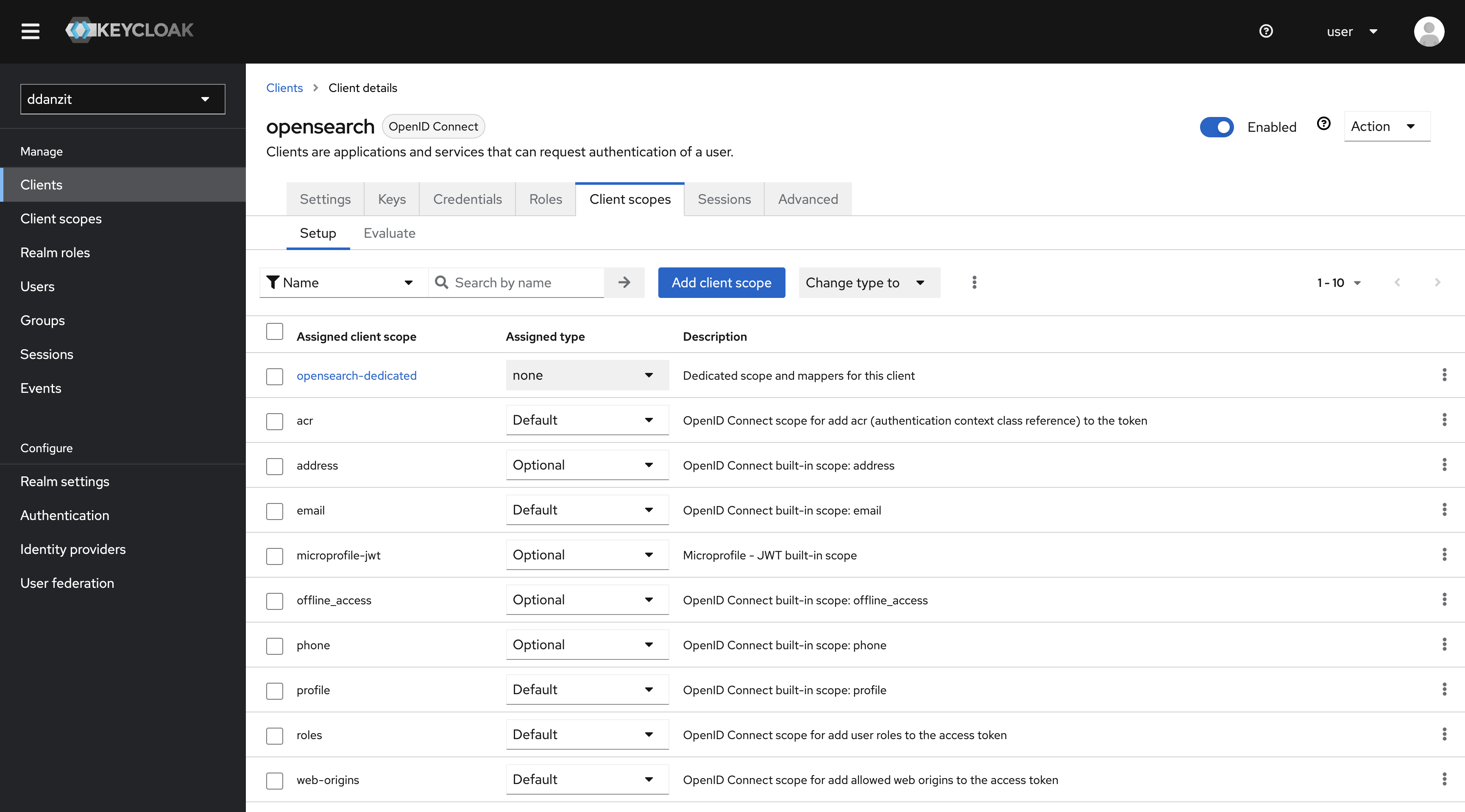
2. KeyCloak OpenSearch User Client Role 생성
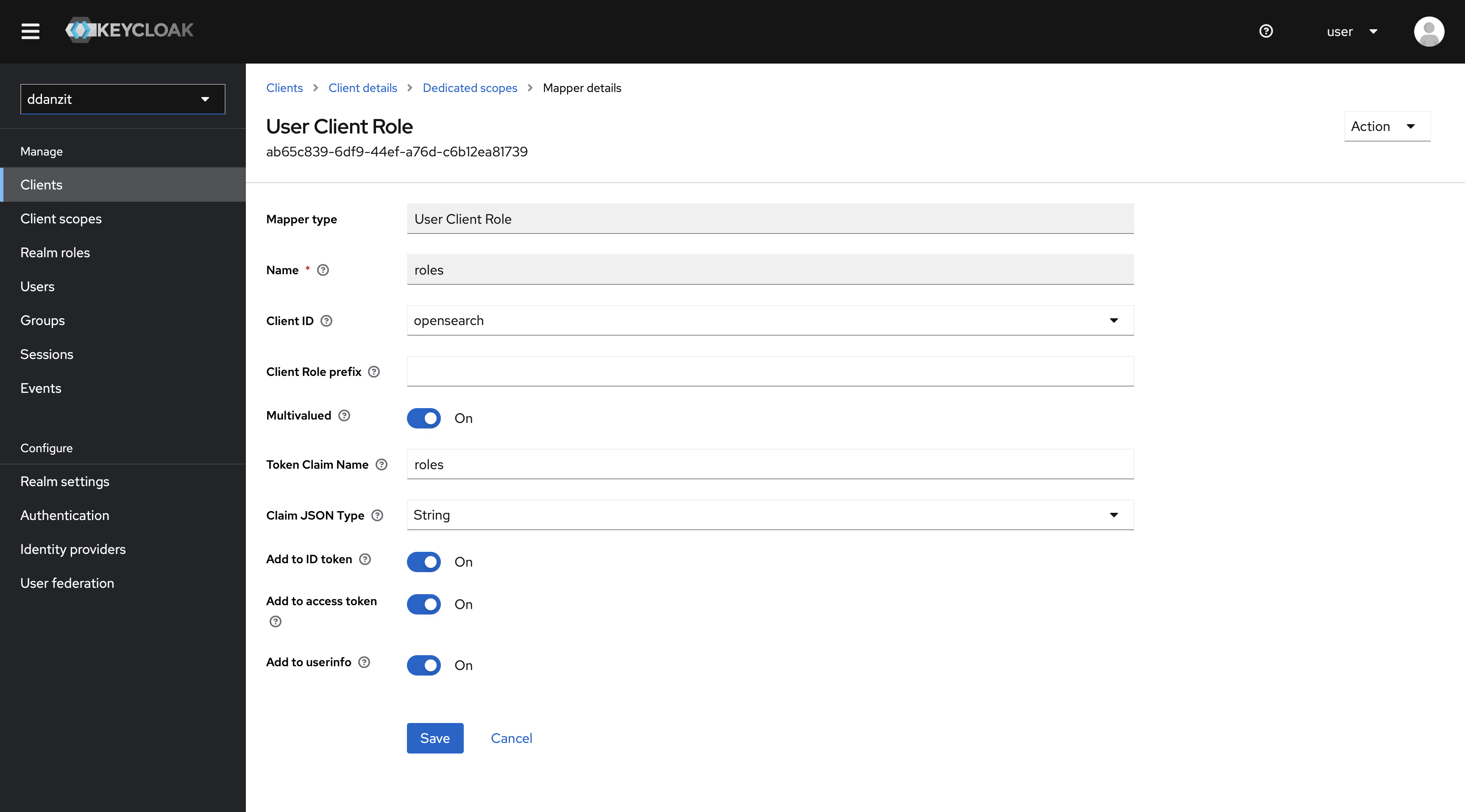
3. OpenSearch 연동 및 설정파일 생성
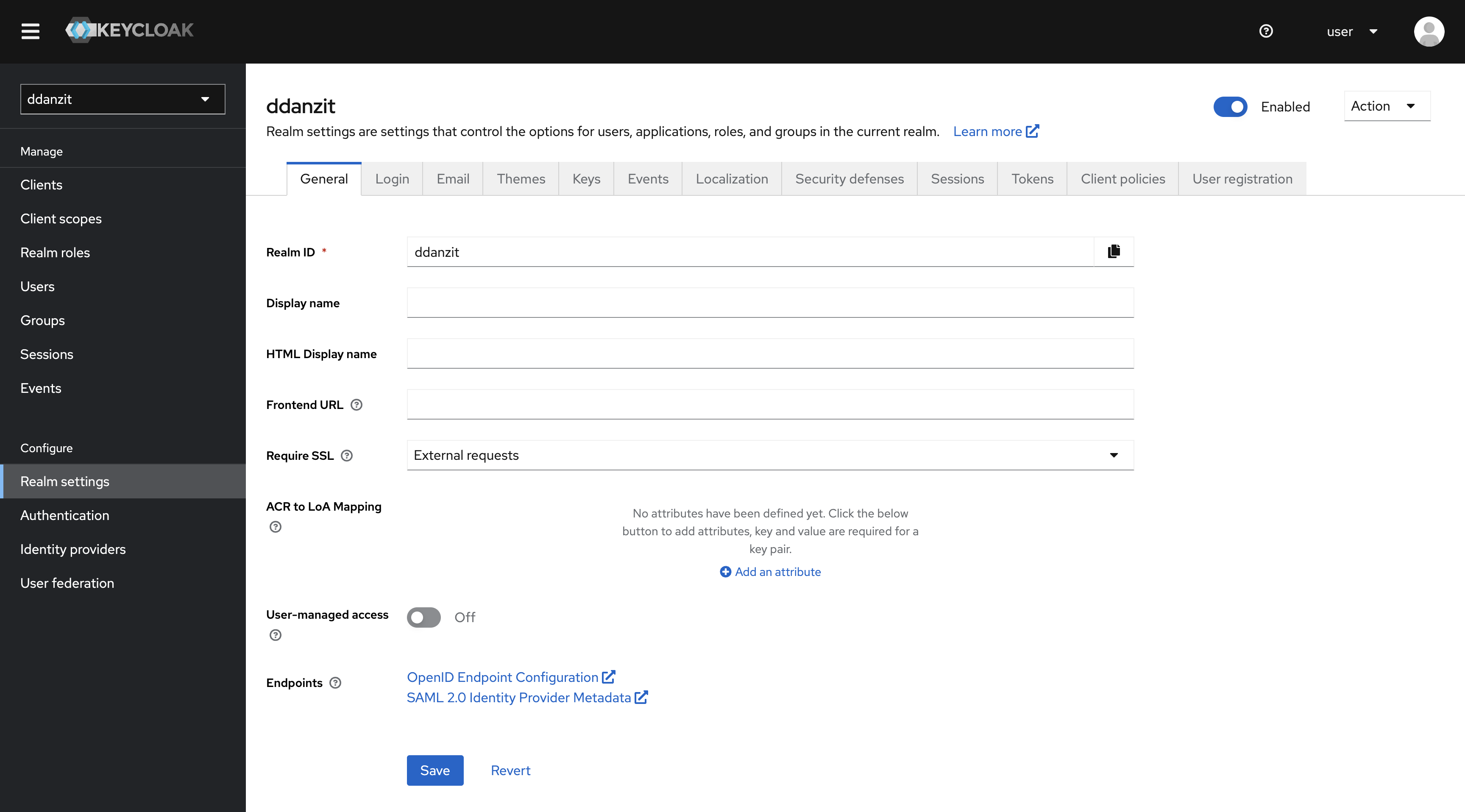
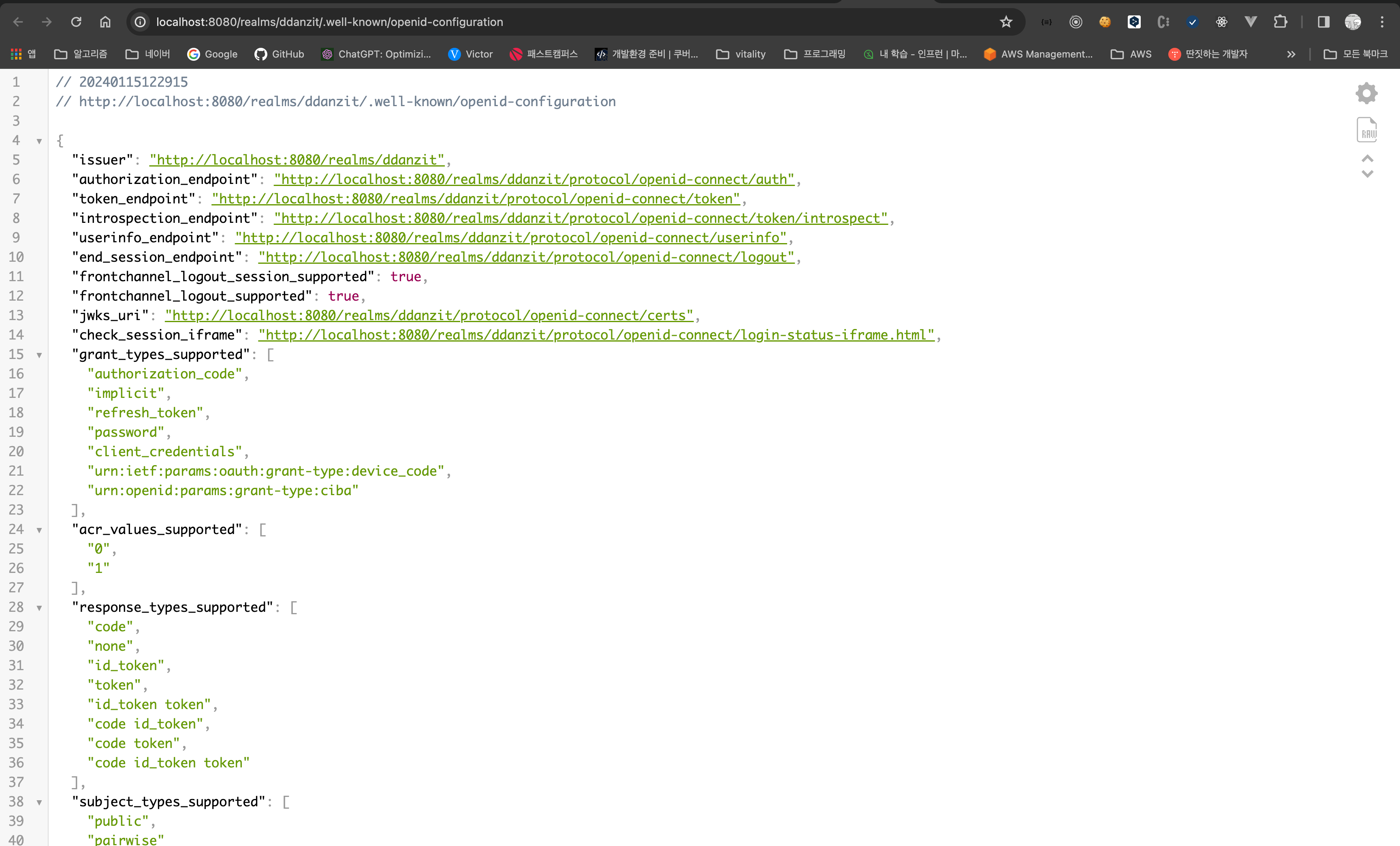
3.1 KeyClock Connect URL 확인
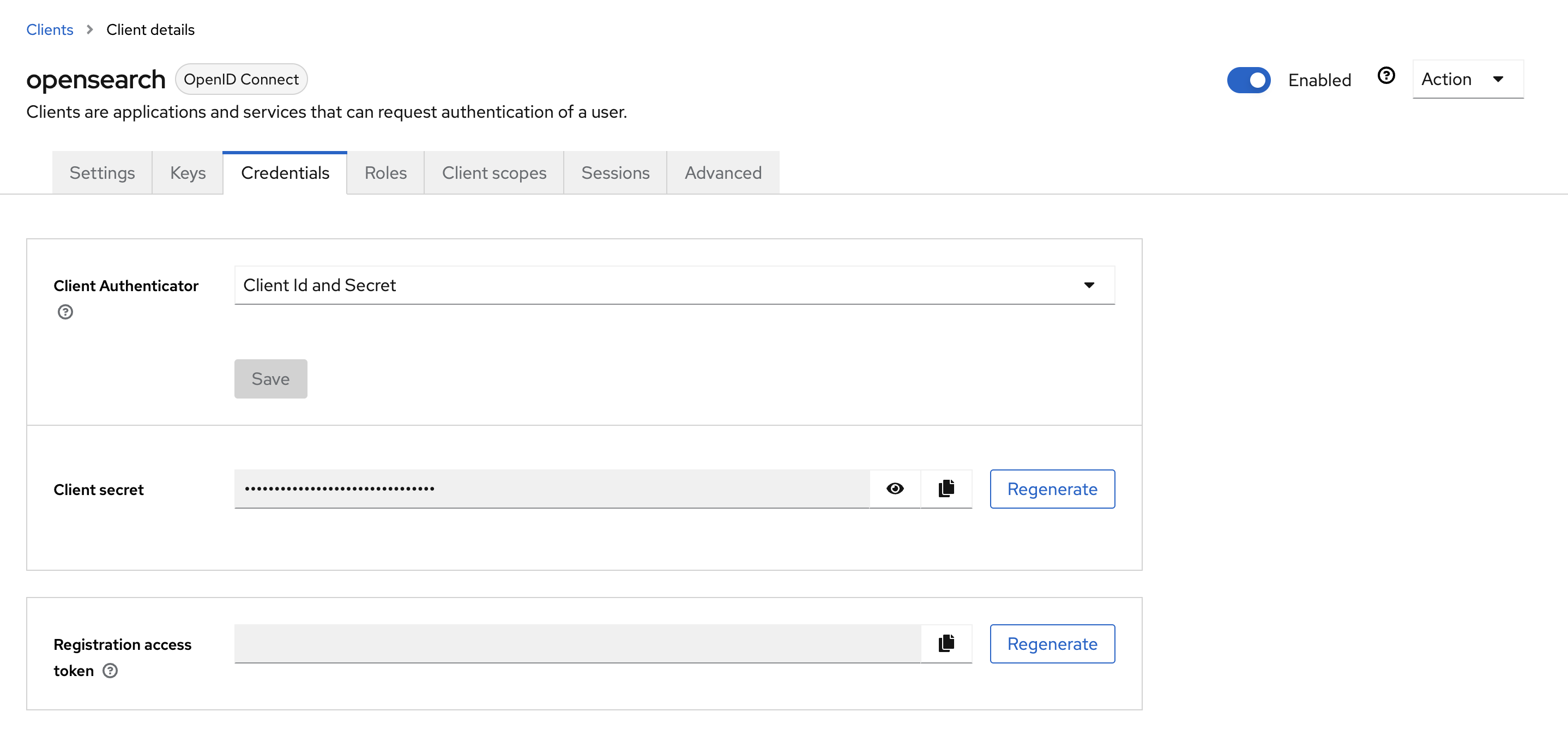
3.2 OpenSearch Client Credential 확인
3.3 config.yml 생성
- https://forum.opensearch.org/t/opensearch-saml-ad-working-but-with-no-basic-authorization-header-warning/13883/2
- https://forum.opensearch.org/t/openid-401-unauthorized-with-keycloak/10364/2
apiVersion: v1 |
config.yml 을 통해 인증 방식과 순서를 설정하면 dashboard 에서 설정된 인증 방식을 확인할 수 있습니다.
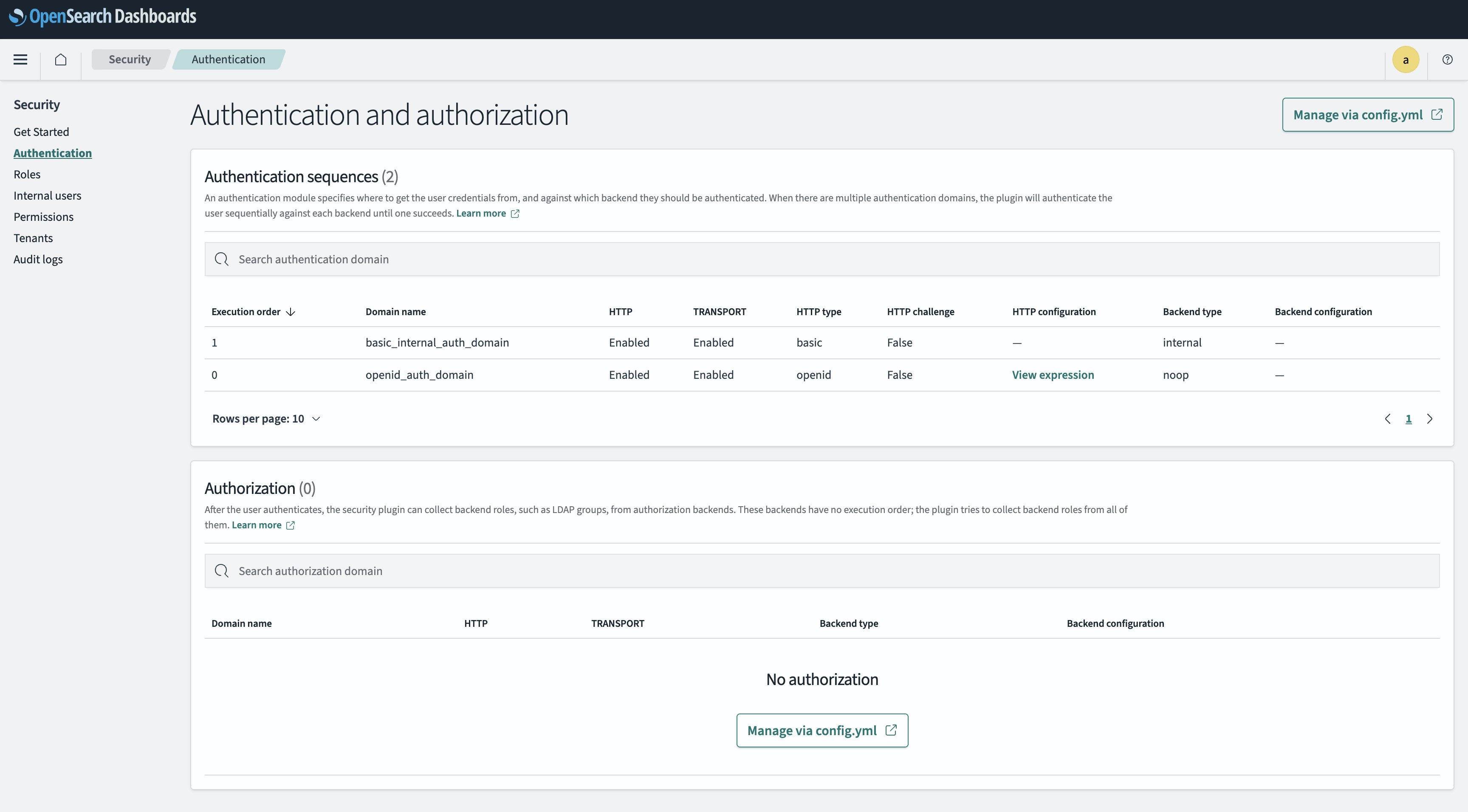
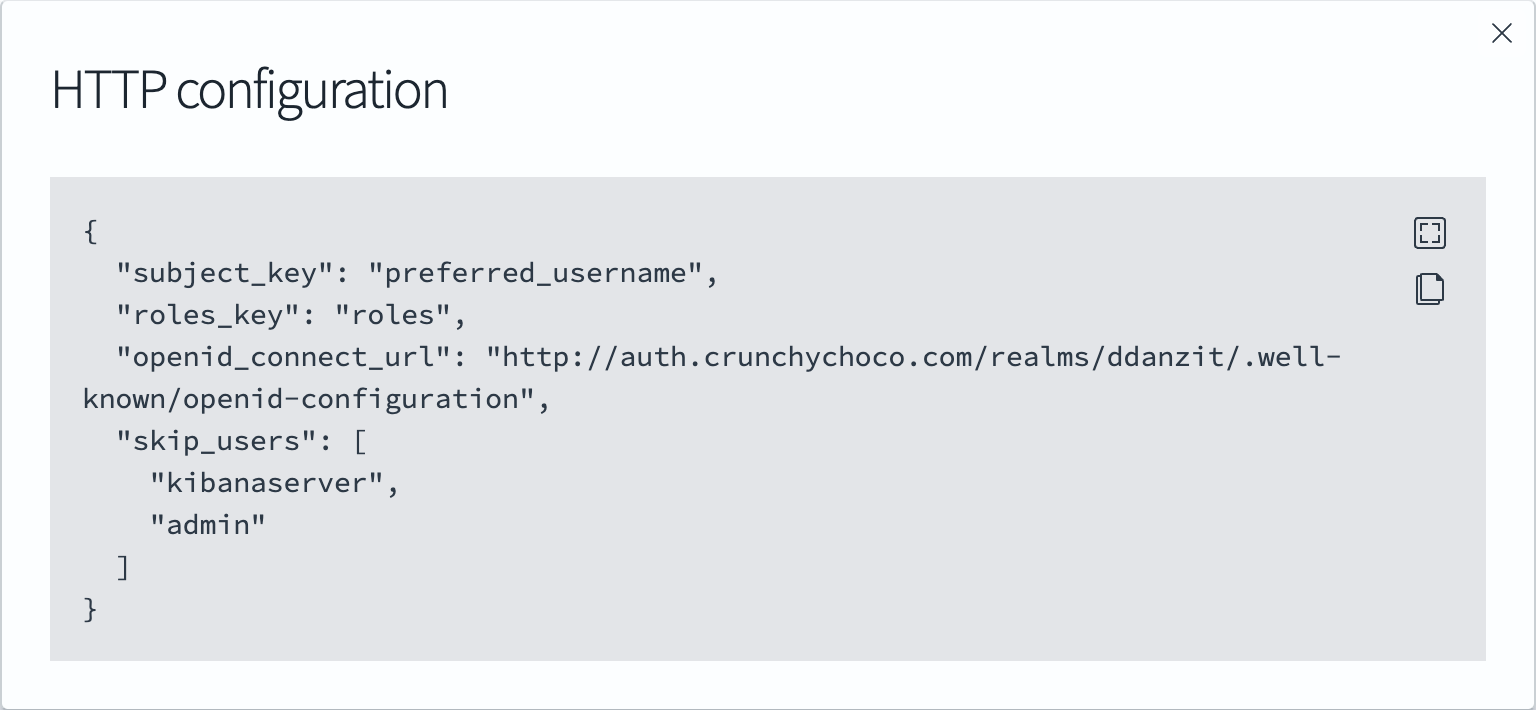
3.4 Opensearch values.yaml 수정
securityConfig: |
3.5 opensearch_dashboards.yml 수정
server: |
3.6 OpenSearch SSO 및 Basic Auth 사용 설정
opensearch_security.auth.type: ["basicauth","openid"] |
3.7 skeycloak 인증 테스트
export CLIENT_ID=opensearch |
3.8 keycloak Json Web Token(JWT) 내용 확인
{ |
No ‘Basic Authorization’ header, send 401 and ‘WWW-Authenticate Basic’
- https://forum.opensearch.org/t/opensearch-dashboards-getting-no-basic-authorization-header-send-401-and-www-authenticate-basic-when-trying-to-login-via-sso/16101/7
- https://forum.search-guard.com/t/no-basic-authorization-header-send-401-and-www-authenticate-basic-while-using-openid-and-basic-auth-domain/1930
- https://opensearch.org/docs/latest/security/configuration/security-admin/
위와 같은 에러가 발생한다면 securityadmin.sh 를 이용하여 설정파일을 적용한다.
kubectl exec \ |
FATAL Error: Multiple Authentication Mode is disabled. To enable this feature, please set up opensearch_security.auth.multiple_auth_enabled: true
opensearch_security.auth.multiple_auth_enabled: true |